What is the future of the Consumer Cybersecurity market? (Part 2)
How much has it changed and what can we expect ahead?
In the first article of this series, we explored how the consumer Cybersecurity market has evolved so far, the forces driving that transformation, and the changes in the vendor landscape.
The next parts will be focused on what we can expect in the future, and how the market is adapting and will need to change even more to accommodate the new behaviours from users and the evolving threats landscape.
Forces Driving Change in Consumer Cybersecurity
The world has changed drastically since the beginnings of the internet and the cybersecurity market, and that transformation has accelerated in the recent years, due to factors like COVID-19, the proliferation of SaaS applications, and artificial intelligence.
People today have an internet connection at home (and at least one router), a web-enabled phone, another device (desktop, laptop, tablet, smart TV), data stored locally (and even more online spread among many locations), a numerous online identities and in some cases an electronic ID as well.
Many of us are working from home, at least partially; some are doing it from an office, and others are connected also from public places, like coffee shops or airports. In the majority of the cases, we share those environments with others: at home, with family and friends; at work, with our colleagues; in public places, with strangers.
This “always-on” situation exposes us to multiple threats - phishing, ransomware, malware, impersonation, identity theft, etc. - that are usually focused on two primary objectives: stealing money or personal data from us.
There’s many security best practices we need in place to secure ourselves when we put all of the above together.
The New Consumer Cybersecurity World Order
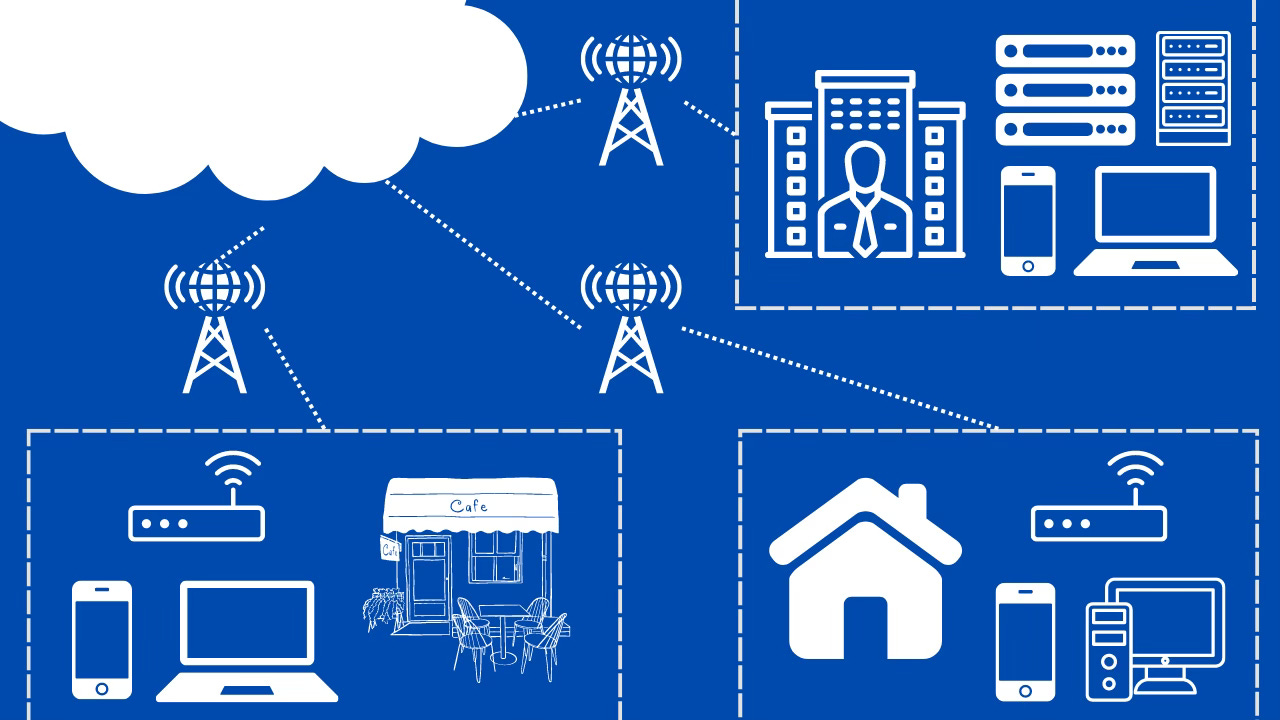
We are living in a world that has blurred the lines of professional and personal lives extremely. Some time ago we were talking about the BYOD (Bring Your Own Device) practices, but now, in this era of remote and hybrid work, we are bringing home to work and vice versa.
Individuals have been using mobile phones provided by their employers as personal devices for some time, and now their laptops and home networks are part of their work environments. The perimeter is long gone, killed by the cloud and SaaS, and security breaches that happen "outside" of the office can affect the businesses that consumers work for.
This is a completely New World Order. Addressing its security and privacy implications requires a different type of approach than the one we have seen so far. The issues not only affect the consumers but also businesses where those work:
A lost or stolen credential of an individual can affect that person but also their employers, as people tend to reuse passwords.
A malware infection in the desktop of a family member of an individual can then jump to a work laptop within the same home network, and from there, to their employers’ environments.
A breached home router can become the way to intercept or alter communications between the employee and its work resources when that person is connected from home.
In this current landscape, it is not only of individuals’ interest to enhance their security, but also something their employers should care about.
Homes need to have a higher security posture if breaches are to be stopped, and devices, networks and identities need to be secured in order to do so. Otherwise, businesses will need to implement strict zero trust measures to prevent their own employees working from home to become their weakest link.
The above is one group of challenges to be solved by vendors. The other one is the consumers’ behaviour itself and the threats they are exposed to that can affect them personally.
Besides a different approach to cybersecurity for individuals than the one we are used until now, there’s a need for interoperability between consumer and business security solutions, and some vendors and actors will be better positioned than others to solve them.
How the vendors will address this?
While there are still many security products for consumers out there, the majority of the market will continue to be consolidated in a handful of vendors as it is today. Microsoft will continue to be the largest by installation share, considering it is included in the Windows operating system by default, and individuals have little motivation to change it.
The rest of the market will continue to consolidate as well, as it had happened under Gen Digital for instance. We will quite probably see other splits of the consumer and business offerings of the vendors that are still catering to both individuals and organisations, which might make sense for them financially, but it’s not compatible with the challenges ahead.
We will also see existing and also new vendors addressing specific market niches until those become big enough to be absorbed by the more established ones.
There are, however, certain actors that will continue to increase their footprint in the cybersecurity market, due to their unique position, like telcos, ISPs, and device manufacturers (mobile phones, routers).
This landscape, combined with the current users behaviours, are opening opportunities for the consumer cybersecurity market to change even more that what we have seen so far.
Opportunities for Consumer Cybersecurity vendors
The consumer cybersecurity market is still in a middle of a transition, and smart organizations can capitalize on the opportunities.
The threats go beyond malware and data loss, and now encompass privacy, identity and access as well as the more traditional solutions.
The challenge for any vendor that expects to succeed in the consumer segment of the security market is the need to compete against Microsoft, free solutions and the apathy of individuals for paying for a security software.
However, while the endpoint security part of the market is more consolidated and follows traditional business models, there are opportunities for growth and innovation. Let’s go through some of them below.
Endpoint
Considering that Defender is available in every PC by default using Microsoft Windows, the strategy that has been pursued by vendors like McAfee for decades, having OEM deals with computer manufacturers, is a way of having a first option to convert PC buyers into paying customers.
Any other vendor that is not pursuing this strategy needs to do the hard work of replacing an existing solution that the user got practically for free. This isn’t usually the case with other operating systems like Mac OS, or when it comes to mobile phones, Smart TVs and other devices.
An important factor at play is that fewer people seem to be usingpersonal computers, as other devices suffice their needs (tablets and phones for their kids), or the work-provided one is used for personal use.
This is, in consequence, shrinking the number of potential customers for the traditional endpoint solutions that need to: a) provide security on other operating systems; b) fight the apathy of users to pay for security; c) fight among each other and replace what came pre-installed.
The challenge and the opportunity for endpoint vendors is then to focus on being the first on the device and having an affordable price for their subscription so they are never replaced, providing extra value to the users so they don’t switch back to a free solution.
The traditional way of being the first is to be pre-installed by a computer manufacturer or to be attached at the point of sale, when the user is purchasing a new device. The other ways include to be delivered seamlessly, for instance, through another service that every user has: their internet connection.
Telcos and ISPs are a growing channel for many vendors. The challenge is that the user needs to execute some action, make some effort, in order to install a security solution provided by their internet service provider.
Every user out there has an internet connection, at home and on-the-go, that aren’t always the same. Every home has a router, provided in the majority of the cases by the ISP, and those devices have access to the users’ network, meaning they could find a way to reduce the effort of the user by detecting potentially unprotected devices and recommend actions on how to improve their security by installing the security software provided by the ISP, including provisioning.
For instance, internet service providers or routers’ manufactures could periodically prompt users to perform a security check of their devices, and use that opportunity to suggest to install additional security solutions.
In a nutshell, endpoint vendors have to think what are the easiest ways to interact with the users and deliver security to them. The real options they have to do so is to:
Be pre-installed in the devices the consumers are purchasing
Utilize Telcos and ISPs as a distribution channel
Any other option is not as effective and do not have the reach of the above. While there are other growing concerns for consumers, like identity protection, which does not yet reach the mass market. Retail is shrinking, traditional resellers don’t reach everyone, so the focus needs to be on those ways that can really get to every user out there.
Beyond the Endpoint
There is a need to protect more than just the endpoints, as users are not only mobile, but also share their networks with others and more devices are inter-connected. The shift is already in progress, from protecting one device to securing the whole household.
This not only applies to the security of the computers, tablets and mobile devices within a home, but also to the online storages the users have, their login credentials into multiple of services (their online identities), and their communications.
Traditional endpoint security providers are already offering packages that can be used to protect all the devices within a household, including additional functionalities like password managers, VPNs and “secure" online storage.
The challenge is that those solutions don’t secure the router, which is a very common vector for attacks, and that homes are having many other connected devices that can be susceptible to breaches.
The Telcos and ISPs are again here well positioned to provide security solutions and services for their subscribers. They already provide smart routers with the goal of becoming the center of the connected homes that include additional applications and services, and in the same way, they could become the security center, if integrated with the rest of the solutions in the household devices.
Providing a secure browsing experience is also an opportunity, where DNS security vendors are partnering with Telcos and ISPs. These companies are in general not the same offering endpoint security. The advantage they have is that their service can be automatically provisioned by the internet service provider without the need for user interaction.
However, at the moment, those providing endpoint security tend not to provide DNS security as well, and integrating both services can provide opportunities for up-selling and cross-selling for vendors and the Telcos and ISPs.
Identity and Privacy
When it comes to Identity and Privacy, the situation is quite different than in the Endpoint:
Apple and Google are already providing a seamless experience when it comes to password management that requires little effort for users to set up and utilize.
Google, Microsoft and Apple credentials are used to log in into many online services.
Google Drive, Microsoft OneDrive and Apple iCloud are widely used to store files online.
VPNs, though, continue to be their own market, but could “easily" be absorbed by traditional vendors. The majority of endpoint security suites for consumers include a VPN, even though the independent providers, like NordVPN and others, continue to have the market leadership at the moment. There have been many other sectors in the past in similar situation that were then absorbed by the largest players, like antispyware tool, personal firewalls, anti-spam solutions.
The interesting shift is in the Identity side of things, which is becoming a growing opportunity where other strong players are looking into, that can create a clash similar to the one the business security market is experiencing with the consolidation of SIEM, SOAR and AnythingDR solutions.
Users have multiple identities spread among many places, and there are very interesting changes coming in this space, with the government-issued digital wallets expected to hit the market at some point in the near future.
With interoperability as a pre-requisite, it would make sense that traditional security solutions would incorporate identity management features that would serve as their online identity verification and authentication tools, storing their digital IDs and their credentials as well.
We see already moves in that direction, with Gen becoming a Founding Premier Member of the OpenWallet Foundation, where other related players like Google, Microsoft, and more traditional IAM players are participating.
The Hybrid World
The world we live in, as described above, poses a number of security challenges that take effort to address. Not only individuals need to care about their home security: their employers should do that as well.
This presents another opportunity for cybersecurity vendors to offer solutions that go beyond the protection of consumers. Those security companies that have not split their home and business lines into different organizations could take advantage of this by offering subscriptions to their business customers that can be extended to their personal devices.
Individuals wouldn’t appreciate to having a business product installed on their family devices, nor handing over control to their employer’s CISO. However, with the appropriate nudge, they would welcome help in securing their household.
Those vendors that have not split have the opportunity to even integrate their consumer solutions into their business ones in a way that employers could ensure the homes of their employees are compliant with the appropriate security best practices.
For instance, the business endpoint security could detect other devices in the home network, and suggest installing there the consumer version of the vendor, at the cost of the employer. Before any privacy advocates find issues, this could be done completely anonymously and in compliance with regulations, with the employer only knowing that the environment of an employee is more or less secure without additional details.
This will help to close security gaps that both employers and employees face and are unequipped to address. Moreover, the vendors that have not split, those that still offer both business and consumer solutions, have another advantage: the opportunity of collecting intelligence from more devices, which in turn, helps them to offer better security.
The future of the Consumer Cybersecurity market
For the past decades, the business cybersecurity market has been getting the most attention and investment, and the consumer segment of this industry became a niche. The availability of free solutions plus the low interest of individuals to pay for software have been weaknesses difficult to address for new and incumbent vendors.
However, this might change sooner rather than later due to changes in the way we work as well as the relevance of protecting not only devices but also identities. There’s not such thing as a pure consumer segment anymore due to the hybrid world, and security breaches in organizations are in many cases started at home.
It’s easy to see a world where Telcos and ISPs become a more prominent cybersecurity channel for consumers, and where the protection of homes against breaches is integrated, to some extent, into the business solutions.
Vendors that want to take advantage of the changes in user behaviours should explore these channels and find ways to become more complete, addressing the identity and privacy concerns from individuals, and providing security for consumers through their employers, which will also increase their chances of protecting their corporate customers against security incidents.
The world has already changed, becoming mostly hybrid, and the immediate future is posed to go even more beyond the endpoint with the upcoming digital national identities and the increased usage of tools both at home and at work.
Any vendor that wants to succeed needs to take advantage of the opportunity this brings to develop a new consumer cybersecurity market that could grow exponentially by leveraging the right channels and an holistic approach for security that doesn’t discriminate between home and the office, as that’s the current reality that will not go away.